Certified Information Systems Security Professional, Part 5 of 9: Network Protocols and Wireless
with expert Kevin Henry
Course description
This course will discuss protocols and structures of communications transmitted across networks. OSI hierarchy and the devices that manage communications and how to protect them. It will end with ports, services and switches and how they must be secured and network based attacks to be prepared for. This course is part of a series covering the ISC(2) Certified Information Systems Security Professional (CISSP).
Prerequisites
This series assumes a good understanding of enterprise networking and networking security. This is part 5 of a 9 part series.
Learning Paths
This course will help you prepare for the following certification and exam:
Certified Information Systems Security Professional
Meet the expert
Kevin is an international author, consultant and international
speaker. He is the official course development writer for ISC2 CISSP, ISACA CRISC and mile2’s C)ISSO. Kevin has been educating IT professionals for over 30 years. He also provides cyber security consulting and support services for organizations around the world. Assisting them with setting up Information Security programs and addressing areas ranging from in-depth risk analysis to policy creation and security awareness.
speaker. He is the official course development writer for ISC2 CISSP, ISACA CRISC and mile2’s C)ISSO. Kevin has been educating IT professionals for over 30 years. He also provides cyber security consulting and support services for organizations around the world. Assisting them with setting up Information Security programs and addressing areas ranging from in-depth risk analysis to policy creation and security awareness.
Course outline
Network Protocols and Devices
OSI Model (31:18)
- Introduction (00:09)
- OSI Model (03:18)
- An Older Model (03:16)
- Data Encapsulation (04:18)
- OSI: Application Layer (01:16)
- OSI: Presentation Layer (01:44)
- OSI: Session Layer (03:02)
- OSI: Transport Layer (04:28)
- OSI: Network Layer (02:57)
- OSI: Data Link Layer (03:44)
- OSI: Physical Layer (01:25)
- Protocols at Each Layer (01:26)
- Summary (00:08)
Network Devices (16:22)
- Introduction (00:09)
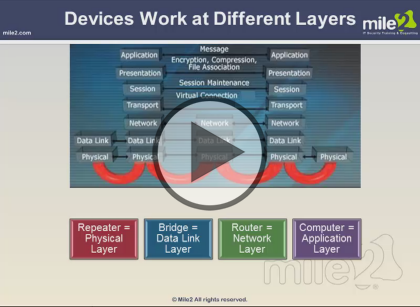
- Devices Work at Different Layers (04:24)
- Networking Devices (00:07)
- Repeater (00:54)
- Hub (01:31)
- Bridge (00:54)
- Switch (02:06)
- Virtual LAN (01:11)
- Router (03:36)
- Gateway (01:18)
- Summary (00:08)
Network Security Sentries (26:34)
- Introduction (00:17)
- Bastion Host (01:49)
- Firewalls (05:18)
- Firewall: First Line of Defense (00:52)
- Firewall Types: Packet Filtering (00:35)
- Firewall Types: Proxy Firewalls (01:25)
- Firewall Types: Circuit-Level Proxy Firewall (00:34)
- Type of Circuit-Level Proxy: SOCKS (00:25)
- Firewall Types: Application-Layer Proxy (01:02)
- Firewall Types: Stateful (01:19)
- Firewall Types: Dymanic Packet-Filtering (00:34)
- Firewall Types: Kernel Proxies (00:40)
- Firewall Placement (01:13)
- Firewall Architecture Types: Screened Host (00:41)
- Firewall Architecture Types: Multi- or Dual-Homed (00:40)
- Firewall Architecture Types: Screened Subnet (00:57)
- IDS: Second Line of Defense (01:32)
- IPS Last Line of Defense (00:46)
- HIPS (01:56)
- Unified Threat Management (02:13)
- UTM Product Criteria (01:28)
- Summary (00:08)
Protocols and Services (17:25)
- Introduction (00:07)
- Protocols (03:05)
- Port and Protocol Relationship (01:02)
- Conceptual Use of Ports (00:23)
- UDP vs. TCP (01:10)
- TCP/IP Suite (01:34)
- Protocols: ARP (00:46)
- Protocols: ICMP (01:06)
- Protocols: SNMP (01:11)
- Protocols: SMTP (00:43)
- Protocols: FTP, TFTP, and Telnet (01:22)
- Protocols: RARP and BootP (00:41)
- Network Service: DNS (01:31)
- Network Service: NAT (02:06)
- Summary (00:24)
- Summary (00:08)
Telephony, VPNs, and Wireless
Telephony (21:11)
- Introduction (00:11)
- PSTN (02:23)
- Remote Access (01:11)
- Dial-Up and Authentication Protocols (02:51)
- Dial-Up Protocol: SLIP (00:44)
- Dial-Up Protocol: PPP (00:58)
- Auhtentication Protocols: PAP and CHAP (03:20)
- Voice Over IP (05:02)
- Private Branch Exchange (01:28)
- PBX Vulnerabilities (01:27)
- PBX Best Practices (01:23)
- Summary (00:08)
VPN (12:10)
- Introduction (00:06)
- Virtual Private Network Technologies (01:20)
- What Is a Tunneling Protocol (01:33)
- Tunneling Protocols: PPTP (00:44)
- Tunneling Protocols: L2TP (00:35)
- Tunneling Protocols: IPSec (00:53)
- IPSec: Network Layer Protection (00:51)
- IPSec (03:23)
- SSL/TLS (02:34)
- Summary (00:08)
Wireless (30:47)
- Introduction (00:09)
- Wireless Technologies: Access Point (01:40)
- Standards Comparison (04:11)
- Wireless Network Topologies (01:04)
- Wi-Fi Network Types (00:46)
- Wireless Technologies: WTLS (01:10)
- Wireless Technologies: Service Set ID (01:17)
- Wireless Technologies: Authenticating to an AP (01:33)
- Wireless Technologies: WEP (03:29)
- Wireless Technologies: More WEP Woes (02:00)
- How WPA Improves on WEP (02:25)
- TKIP (01:47)
- The WPA MIC Vulnerability (00:57)
- 802.11i: WPA2 (01:29)
- WPA and WPA2 Mode Types (01:18)
- WPA-PSK Encryption (01:10)
- Wireless Technologies: WAP (01:11)
- WTLS (02:54)
- Summary (00:08)
Network-Based Attacks (09:39)
- Introduction (00:06)
- Wireless Technologies: Common Attacks (01:44)
- Wireless Technologies: War Driving (00:50)
- Kismet (00:45)
- Wireless Technologies: Countermeasures (01:29)
- Network Based Attacks (01:06)
- ARP Attacks and DDoS Issues (01:34)
- Man-in-the-Middle (00:26)
- Traceroute Operation (01:06)
- Summary (00:21)
- Summary (00:08)