Certified Information Systems Security Professional, Part 4 of 9: Cryptography and Net Topologies
with expert Kevin Henry
Course description
This course covers symmetric and asymmetric cryptography and their history will be covered along with topics like Public key infrastructure, and various attacks. Also network and communication security will be discussed with topics inluding: network topologies, cabling and finally end with looking at network solutions. This course is part of a series covering the ISC(2) Certified Information Systems Security Professional (CISSP).
Prerequisites
This series assumes a good understanding of enterprise networking and networking security. This is part 4 of a 9 part series.
Learning Paths
This course will help you prepare for the following certification and exam:
Certified Information Systems Security Professional
Meet the expert
Kevin is an international author, consultant and international
speaker. He is the official course development writer for ISC2 CISSP, ISACA CRISC and mile2’s C)ISSO. Kevin has been educating IT professionals for over 30 years. He also provides cyber security consulting and support services for organizations around the world. Assisting them with setting up Information Security programs and addressing areas ranging from in-depth risk analysis to policy creation and security awareness.
speaker. He is the official course development writer for ISC2 CISSP, ISACA CRISC and mile2’s C)ISSO. Kevin has been educating IT professionals for over 30 years. He also provides cyber security consulting and support services for organizations around the world. Assisting them with setting up Information Security programs and addressing areas ranging from in-depth risk analysis to policy creation and security awareness.
Course outline
Asymmetric Cryptography and PKI
Asymmetric Cryptography (30:59)
- Introduction (00:15)
- Asymmetric Cryptography (01:38)
- Public Key Cryptography Advantages (03:54)
- Asymmetric Algorithm Disadvantages (01:18)
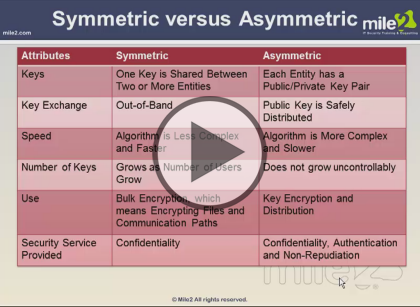
- Symmetric vs. Asymmetric (04:00)
- Asymmetric Algorithms (02:11)
- Asymmetric Algorithm: Diffie-Hellman (01:30)
- Asymmetric Algorithms: RSA (01:40)
- Asymmetric Algorithms: El Gamal and ECC (00:43)
- Example of Hybrid Cryptography (02:31)
- When to Use Which Key (02:05)
- Using the Algorithm Types Together (01:09)
- Digital Signatures (03:01)
- Digital Signature and MAC Comparison (01:14)
- What if You Need All of the Services? (02:14)
- U.S. Government Standard (01:21)
- Summary (00:08)
Public Key Infrastructure (14:15)
- Introduction (00:06)
- Why Do We Need a PKI (00:00)
- Environment (01:06)
- PKI and Its Components (03:11)
- CA and RA Roles (01:08)
- Let's Walk Through an Example (02:05)
- Digital Certificates (00:49)
- What Do You Do with a Certificate? (03:46)
- Components of PKI: Repository and CRLs (01:53)
- Summary (00:08)
Cryptography and Attacks (44:01)
- Introduction (00:28)
- Cryptography and Attacks (00:00)
- Steganography (03:26)
- Key Management (04:50)
- Link vs. End-to-End Encryption (02:16)
- End-to-End Encryption (00:36)
- Email Standards (02:37)
- Secure Protocols (01:47)
- SSL and the OSI Model (03:00)
- SSL Connection Setup (02:50)
- Secure Email Standard (01:01)
- SSH Security Protocol (01:04)
- Network Layer Protection (01:23)
- IPSec Key Management (01:20)
- Key Issues Within IPSec (00:45)
- IPSec Handshaking Process (02:14)
- SAs in Use (01:49)
- IPSec Is a Suite of Protocols (01:26)
- IPSec Modes of Operation (05:08)
- Attacks on Cryptosystems (03:16)
- More Attacks (01:49)
- Summary (00:37)
- Summary (00:08)
Network Connections
Network Communications Security (11:30)
- Introduction (00:07)
- Network Security Issues (01:49)
- Network and Communications Security (01:38)
- Communications Security (00:40)
- Network Security Methods (04:00)
- Network-Based Security Problems (03:06)
- Summary (00:08)
Network Topologies (31:59)
- Introduction (00:14)
- Network Topologies: Physical Layer (00:49)
- Topology Type: Bus (01:42)
- Topology Type: Ring (01:55)
- Topology Type: Star (01:07)
- Network Topologies: Mesh (02:07)
- Summary of Topologies (01:48)
- LAN Media Access Technologies (06:18)
- One Goal of Media Access Technologies (01:58)
- Transmission Types: Analog and Digital (01:57)
- Transmission Types: Synchronous and Asynchronous (05:45)
- Two Types of Carrier Sense Multiple Access (01:20)
- Transmission Types: Number of Receivers (01:05)
- Media Access Technologies: Ethernet (01:55)
- Media Access Technologies: Token Passing (01:00)
- Media Access Technologies: Polling (00:42)
- Summary (00:08)
Network Technologies and Cabling (45:15)
- Introduction (00:08)
- Cabling (03:40)
- Cabling Types: Coaxial (01:10)
- Cabling Types: Twisted Pair (02:35)
- Cabling Issues: Plenium-Rated (00:59)
- Types of Networks (02:37)
- Network Technologies (03:12)
- Network Configurations (01:53)
- MAN Technologies: SONET (02:13)
- Wide Area Network Technologies (02:27)
- WAN Technologies Are Circuit or Packet Switched (02:35)
- Cicuit Switching (02:01)
- WAN Technologies: ISDN (03:18)
- ISDN Service Types (02:03)
- WAN Technologies: DSL (01:54)
- WAN Technologies: Cable Modem (01:34)
- Packet Switching (01:15)
- WAN Technologies: Packet Switched (01:00)
- Packet Switched Networks (01:52)
- WAN Technologies: X.25 (00:42)
- WAN Technologies: Frame Relay (01:28)
- WAN Technologies: ATM (01:24)
- Multiplexing (01:40)
- Permanent Virtual Circuits (01:17)
- Summary (00:08)