Course description
Writing secure applications in today's environment means we need to take our coding skills and approach up to a whole new level. Hackers are finding new ways to exploit us in ways that we used to think were safe. In this course we look at building secure applications from the mindset of the hacker, and what a developer can do to avoid the front pages of the latest exploit. We go thru secure coding principles and tools you can use to uncover attack vectors, look at patterns for reducing our risk, and the explore some top exploits that hackers use to steal our data.
Prerequisites
This course is for users with experience with developing web applications using C# or other object oriented programming languages.
Learning Paths
This course is part of the following LearnNowOnline SuccessPaths™:
OWASP
Meet the expert
Mike Benkovich delivers technical presentations around the U.S. as a consultant, trainer, and former Developer Evangelist for Microsoft. He has worked in a variety of professional roles including architect, project manager, developer, and technical writer. Mike is also an author of two books, published by WROX Press and APress, that show developers how to get the most from their SQL databases. Since appearing in the 1994 Microsoft DevCast, Mike has presented technical information at seminars, conferences, and corporate boardrooms across America.
Course outline
Avoiding Hacker Tricks
Introduction (27:03)
- Introduction (00:29)
- Is Security Important? (01:13)
- The Perfect Scenario (00:23)
- The Real World (01:03)
- Attackers advantage & defenders dilemma (01:33)
- Build Secure Apps (01:19)
- Security Mindset (03:46)
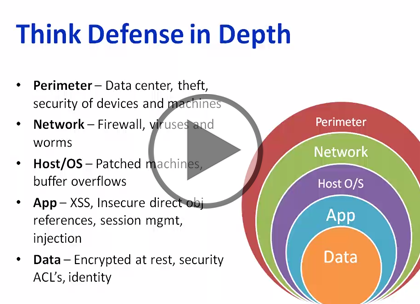
- Think Defense in Depth (02:58)
- Secure Coding Techniques (03:21)
- Threat Modeling Steps (02:04)
- Consider STRIDE (02:55)
- Free Tools Available (01:07)
- Demo: Threat Modeling Tools (04:34)
- Summary (00:12)
Know Your Threats (05:22)
- Introduction (00:17)
- Common Threats (01:33)
- Secure Coding (01:22)
- OWASP Top 10 Security Exploits (00:48)
- Demo: OWASP (01:08)
- Summary (00:12)
Cross Site Scripting (13:23)
- Introduction (00:16)
- Most Common Security Risks (00:10)
- Cross Site Scripting (00:58)
- Demo: Cross Site Scripting (03:55)
- Demo: Prevent Scripting (03:14)
- Demo: Persistent Scripting (02:54)
- Cross Site Scripting (01:34)
- Summary (00:19)
SQL Injection Attack (17:53)
- Introduction (00:20)
- Most Common Security Risks (00:07)
- SQL Injection (00:41)
- For Example...Authentication (01:36)
- SQL Injection (00:34)
- Demo: SQL Injection (01:03)
- Demo: Stopping Injection (01:58)
- Demo: LINQ to SQL (05:14)
- Demo: Run Application (00:55)
- Demo: URL SQL Injection (03:19)
- SQL Injection (01:40)
- Summary (00:19)
Insecure Object Reference (15:48)
- Introduction (00:18)
- Insecure Object Direct Reference (00:52)
- Demo: Insecure Object Direct Reference (01:32)
- Demo: Indirect Reference Map (05:55)
- Demo: Encryption (06:12)
- Insecure Direct Object Reference (00:46)
- Summary (00:12)
Integer Overflow (04:46)
- Introduction (00:17)
- Most Common Security Risks (00:15)
- Integer Overflow (00:33)
- Preventing Integer Overflow (00:31)
- Demo: Integer Overflow (02:28)
- Integer Overflow (00:32)
- Summary (00:08)