Course description
Take a look at application security and put your development skills under a microscope. Specifically, explore all the things that might go wrong in your application development including cross-site scripting, SQL Injection attacks, and buffer overflows. But don’t worry, it won’t be all doom and gloom in this course. You'll also delve into some security frameworks and controls that can be put in place to help to better protect your applications from being compromised. This course is part of a series covering the CompTIA Advanced Security Practitioner (CASP).
Prerequisites
This course assumes that the student has familiarity with information technology and basic networking. The student should also be familiar with basic security concepts, whether through the CompTIA Advanced Security Practitioner Part 1 course or outside study. No scripting or “hacking” experience is required.
Meet the expert
David Bigger is the lead trainer at Bigger IT Solutions. He has been information technology for a little over 20 years and has been training all over the US. He has worked with companies like US Military, Lockheed Martin, General Dynamics, Dominos Pizza, University of Utah and Expedia
Course outline
Threats and Mitigation
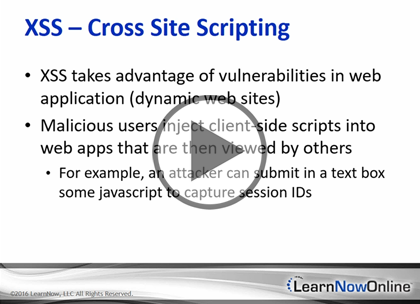
Cross Site Scripting (20:00)
- Introduction (00:21)
- Application Security (03:40)
- Terms (02:02)
- Vulnerabilities (00:45)
- XSS - Cross Site Scripting (02:03)
- XSS (01:04)
- XSS - What Can Happen? (04:36)
- XSS - How? (01:54)
- Defending Against XSS (03:10)
- Summary (00:20)
SQL Injection (17:07)
- Introduction (00:25)
- SQL Injection (03:04)
- What Can Happen? (04:46)
- What to Look for (02:03)
- Defending SQL Injections (02:36)
- Buffer Overflows (03:49)
- Summary (00:21)
Session ID (18:42)
- Introduction (00:24)
- Session IDs (05:58)
- How to Get Session IDs (06:21)
- Stop Taking My ID (05:37)
- Summary (00:20)
Controls (20:19)
- Introduction (00:25)
- Controls for Application Security (01:00)
- Secure Coding Practices (03:31)
- What Kind of Practices? (03:16)
- WAF (01:48)
- What Can a WAF Do (01:03)
- Where a WAF Goes (03:28)
- Code Reviews (05:23)
- Summary (00:21)
Security Frameworks (15:52)
- Introduction (00:19)
- Security Frameworks (02:32)
- Standard Libraries (04:14)
- OWASP (02:41)
- ISO/IEC 27000 (01:08)
- WASC (01:02)
- WS-Security (03:31)
- Summary (00:20)